Software wallets offer convenient access to cryptocurrencies through apps or browsers, allowing quick transactions but are more vulnerable to hacking due to constant internet connectivity. Hardware wallets, by storing private keys offline on physical devices, provide enhanced security against cyber threats and unauthorized access. Choosing between the two depends on balancing ease of use with the need for robust protection of digital assets.
Table of Comparison
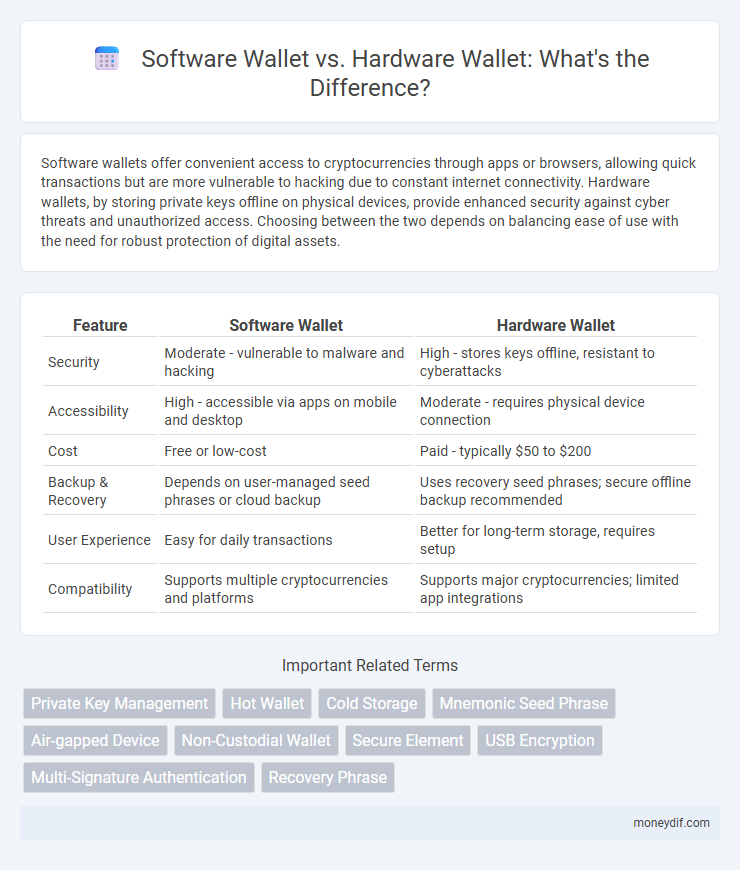
| Feature | Software Wallet | Hardware Wallet |
|---|---|---|
| Security | Moderate - vulnerable to malware and hacking | High - stores keys offline, resistant to cyberattacks |
| Accessibility | High - accessible via apps on mobile and desktop | Moderate - requires physical device connection |
| Cost | Free or low-cost | Paid - typically $50 to $200 |
| Backup & Recovery | Depends on user-managed seed phrases or cloud backup | Uses recovery seed phrases; secure offline backup recommended |
| User Experience | Easy for daily transactions | Better for long-term storage, requires setup |
| Compatibility | Supports multiple cryptocurrencies and platforms | Supports major cryptocurrencies; limited app integrations |
Introduction to Software and Hardware Wallets
Software wallets store cryptocurrency keys on internet-connected devices such as smartphones, computers, or tablets, offering ease of access and convenience for frequent transactions. Hardware wallets keep private keys offline on specialized physical devices, providing enhanced security against hacking and malware risks. Choosing between software and hardware wallets depends on the balance between accessibility preferences and the need for higher protection of digital assets.
Key Differences Between Software and Hardware Wallets
Software wallets store private keys on internet-connected devices, offering ease of access and convenience for frequent transactions but posing higher risks of hacking or malware attacks. Hardware wallets, by contrast, keep private keys offline on physical devices, significantly enhancing security by isolating keys from online environments, making them ideal for long-term storage. The choice hinges on balancing security needs versus transaction frequency, with software wallets suited for daily use and hardware wallets preferred for safeguarding substantial cryptocurrency holdings.
Security Features: Software Wallets vs Hardware Wallets
Software wallets store private keys on internet-connected devices, making them more vulnerable to malware, phishing attacks, and remote hacking attempts. Hardware wallets keep private keys isolated within a physical device, providing robust protection against online threats by requiring user interaction for every transaction. These hardware devices employ secure elements and PIN codes, significantly enhancing security compared to software wallets.
Accessibility and Convenience Comparison
Software wallets offer superior accessibility due to their compatibility with smartphones and computers, enabling users to manage cryptocurrencies anytime and anywhere with internet access. Hardware wallets prioritize security by storing private keys offline, but their physical nature can limit convenience, requiring users to carry the device and connect it to a computer for transactions. The trade-off between software wallets' ease of use and hardware wallets' enhanced protection depends on the user's preference for accessibility or security in cryptocurrency management.
Supported Cryptocurrencies: Flexibility of Each Wallet Type
Software wallets generally support a wider range of cryptocurrencies, including most ERC-20 tokens and emerging altcoins, making them highly flexible for diverse portfolios. Hardware wallets, while more secure, typically support a curated list of major coins like Bitcoin, Ethereum, and popular tokens, focusing on robust protection rather than extensive compatibility. Users prioritizing maximum asset variety often prefer software wallets, whereas those emphasizing security select hardware wallets with essential cryptocurrency support.
Backup and Recovery Options
Software wallets offer convenient backup options, typically involving encrypted seed phrases or private keys stored digitally, enabling quick recovery on multiple devices. Hardware wallets provide enhanced security by storing private keys offline and require physical access for recovery, often involving a recovery seed phrase that must be securely preserved. Both wallet types emphasize the importance of safeguarding recovery phrases to prevent unauthorized access and ensure full access restoration.
Cost Analysis: Software Wallets vs Hardware Wallets
Software wallets generally offer lower upfront costs as they are often free or have minimal fees, making them accessible for everyday users. Hardware wallets require a higher initial investment, typically ranging from $50 to $200, but provide enhanced security by storing private keys offline. Over time, software wallets may incur hidden costs related to security breaches or data loss, while hardware wallets reduce these risks, potentially saving users from expensive recovery processes.
User Experience and Interface Design
Software wallets offer intuitive interfaces with seamless integration across devices, enhancing user experience through ease of access and real-time transaction tracking. Hardware wallets prioritize security by isolating private keys offline but often feature minimalistic displays and physical buttons, which can limit interface sophistication and slow user interaction. Balancing robust security with user-friendly design remains a critical challenge distinguishing hardware wallets from their software counterparts.
Ideal Use Cases for Each Wallet Type
Software wallets are ideal for frequent transactions and quick access, making them suitable for everyday users and those who prioritize convenience on mobile devices or desktops. Hardware wallets excel in long-term storage and enhanced security, perfect for investors holding significant cryptocurrency amounts offline to protect against hacks. Choosing between them depends on balancing usability and security based on transaction frequency and asset value.
Final Verdict: Choosing the Right Wallet for Your Needs
Software wallets offer convenient, quick access to cryptocurrency through smartphones or desktops, ideal for frequent traders and small holdings. Hardware wallets provide enhanced security by storing private keys offline, making them the best choice for long-term investors and large asset protection. Selecting the right wallet depends on balancing security needs, usage frequency, and asset value to fit individual cryptocurrency management preferences.
Important Terms
Private Key Management
Private key management in software wallets involves storing keys digitally on devices vulnerable to malware and hacking, increasing security risks. Hardware wallets store private keys offline within a physical device, providing enhanced protection against cyber threats and unauthorized access.
Hot Wallet
Hot wallets, which are software-based and connected to the internet, offer convenient but less secure access to cryptocurrencies compared to offline hardware wallets that provide enhanced protection against cyber threats.
Cold Storage
Cold storage refers to offline cryptocurrency wallets that store private keys without internet access, significantly reducing hacking risks; hardware wallets like Ledger and Trezor are leading cold storage devices offering enhanced security by isolating keys within physical devices. In contrast, software wallets, although convenient for frequent transactions, remain vulnerable to malware and phishing attacks due to their online or connected nature.
Mnemonic Seed Phrase
Mnemonic seed phrases serve as the crucial recovery mechanism for both software and hardware wallets, enabling users to restore access to their cryptocurrency holdings securely. Hardware wallets store these seed phrases offline, providing enhanced protection against malware and hacking, while software wallets often keep them digital, which increases convenience but also exposure to cyber threats.
Air-gapped Device
An air-gapped device enhances security by isolating a software wallet from internet connectivity, reducing exposure to cyber threats and malware attacks. Hardware wallets offer secure offline storage of private keys, but pairing them with an air-gapped device can provide an extra layer of protection against remote hacking attempts.
Non-Custodial Wallet
Non-custodial wallets give users full control of private keys, differing between software wallets such as mobile or desktop apps that offer convenience and immediate access, and hardware wallets that provide enhanced security by storing keys offline in physical devices. Software wallets prioritize ease of use and accessibility, while hardware wallets minimize exposure to cyber threats by isolating keys from internet-connected environments.
Secure Element
Secure Element (SE) is a tamper-resistant hardware component designed to securely store cryptographic keys and execute sensitive operations, offering higher protection in hardware wallets compared to software wallets that rely on general-purpose devices vulnerable to malware. Hardware wallets embed SEs to isolate private keys from external threats, whereas software wallets store keys on internet-connected devices, increasing risk of compromise.
USB Encryption
USB encryption enhances security for software wallets by protecting private keys stored on USB devices from unauthorized access and malware breaches, whereas hardware wallets use embedded secure elements to encrypt and isolate keys, providing stronger protection against physical theft and hacking attempts. Software wallets rely on USB encryption for secure backup and transfer of encrypted wallet data, but hardware wallets inherently combine USB connectivity with dedicated cryptographic hardware to prevent key extraction and ensure transaction integrity.
Multi-Signature Authentication
Multi-signature authentication enhances security by requiring multiple private keys to authorize transactions, significantly reducing the risk of unauthorized access in both software and hardware wallets. Hardware wallets offer superior protection for multi-signature setups by storing keys in isolated, tamper-resistant devices, while software wallets provide more convenience but are more vulnerable to malware and hacking threats.
Recovery Phrase
Recovery phrases are critical for restoring access to cryptocurrency wallets, with software wallets storing them digitally, posing risks of online theft, while hardware wallets keep them offline, enhancing security against hacking. Users relying on hardware wallets benefit from encrypted physical storage of recovery phrases, reducing exposure to malware compared to software wallet recovery methods.
Software Wallet vs Hardware Wallet Infographic
 moneydif.com
moneydif.com