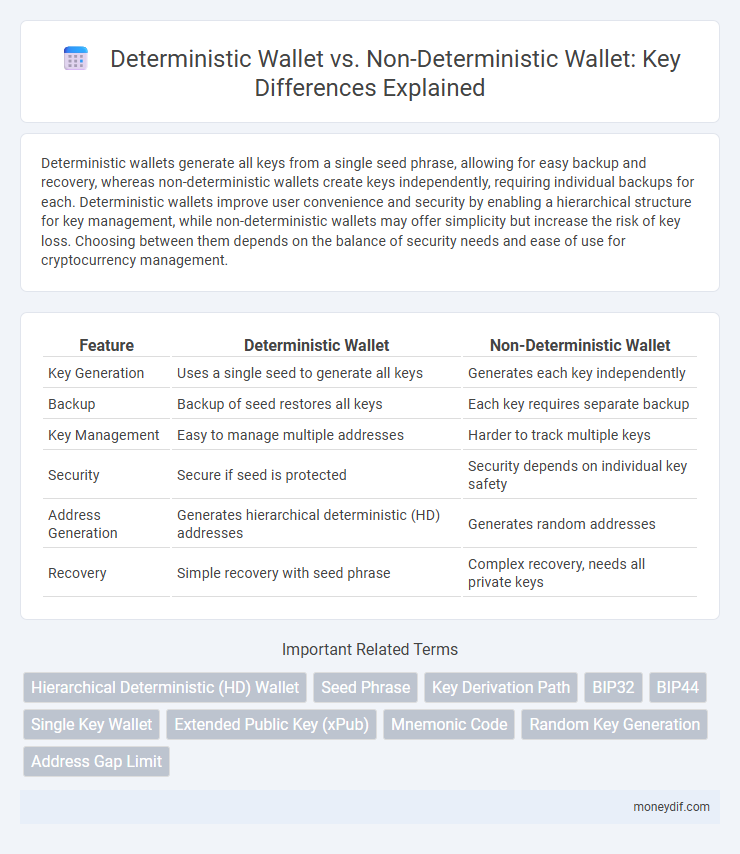
Deterministic wallets generate all keys from a single seed phrase, allowing for easy backup and recovery, whereas non-deterministic wallets create keys independently, requiring individual backups for each. Deterministic wallets improve user convenience and security by enabling a hierarchical structure for key management, while non-deterministic wallets may offer simplicity but increase the risk of key loss. Choosing between them depends on the balance of security needs and ease of use for cryptocurrency management.
Table of Comparison
| Feature | Deterministic Wallet | Non-Deterministic Wallet |
|---|---|---|
| Key Generation | Uses a single seed to generate all keys | Generates each key independently |
| Backup | Backup of seed restores all keys | Each key requires separate backup |
| Key Management | Easy to manage multiple addresses | Harder to track multiple keys |
| Security | Secure if seed is protected | Security depends on individual key safety |
| Address Generation | Generates hierarchical deterministic (HD) addresses | Generates random addresses |
| Recovery | Simple recovery with seed phrase | Complex recovery, needs all private keys |
Introduction to Cryptocurrency Wallets
Deterministic wallets generate all keys from a single seed phrase, enabling easy backup and recovery, while non-deterministic wallets create keys independently, complicating backup processes. Deterministic wallets follow hierarchical deterministic (HD) standards such as BIP32, enhancing security and convenience for managing multiple addresses. Non-deterministic wallets, often called legacy wallets, lack structured key derivation, making them less efficient for modern cryptocurrency management.
What is a Deterministic Wallet?
A deterministic wallet generates all private keys from a single seed phrase, allowing users to recover their entire wallet using just that seed. This structure creates a hierarchical tree of keys, enabling efficient backup and management of multiple addresses without storing each private key individually. Deterministic wallets enhance security and convenience by simplifying key recovery and reducing the risk of key loss.
What is a Non-Deterministic Wallet?
A Non-Deterministic Wallet generates each private key independently using random data, lacking a structured algorithmic sequence. This type of wallet does not rely on a single seed phrase for backup, making key recovery more complex if keys are lost. Security depends on strong random key generation but lacks the convenience of hierarchical key derivation found in deterministic wallets.
Key Differences Between Deterministic and Non-Deterministic Wallets
Deterministic wallets generate all key pairs from a single seed phrase, allowing easy backup and recovery through a master seed, while non-deterministic wallets create keys independently, requiring individual backups for each key. Deterministic wallets enable hierarchical deterministic (HD) structures, improving privacy by generating unique addresses per transaction; non-deterministic wallets lack this feature, leading to potential address reuse. Key management efficiency and enhanced security in deterministic wallets contrast with the complexity and higher risk of key loss in non-deterministic wallets.
Seed Phrase and Backup: Deterministic Wallets
Deterministic wallets generate all private keys from a single seed phrase, enabling easy backup and recovery with just one phrase. This seed phrase, typically a 12-24 word mnemonic, allows users to restore the entire wallet and its transaction history without needing multiple key backups. In contrast, non-deterministic wallets require individual private key backups, complicating recovery if any are lost.
Security Features in Non-Deterministic Wallets
Non-deterministic wallets generate each private key independently, enhancing security by isolating key compromise risks and preventing the exposure of multiple keys if one is breached. Their lack of a seed phrase eliminates vulnerabilities associated with seed extraction or recovery phrase attacks, reducing the attack surface. However, non-deterministic wallets require meticulous key management practices since loss of any private key can result in irreversible loss of assets.
Use Cases: When to Choose Each Wallet Type
Deterministic wallets, also known as HD wallets, are ideal for users needing easy backup and recovery through a single seed phrase, making them suitable for everyday transactions, multi-account management, and portfolio diversification. Non-deterministic wallets, or legacy wallets, provide enhanced privacy by generating independent keys, preferred by users requiring isolated transaction histories and heightened security for specific use cases like cold storage. Choosing between these wallet types depends on balancing convenience, backup simplicity, and privacy requirements in cryptocurrency management.
Advantages of Deterministic Wallets
Deterministic wallets generate all private keys from a single seed phrase, allowing users to easily back up and restore their entire wallet with one mnemonic. This structure provides enhanced security and convenience, as users need to safeguard only the seed rather than individual keys. Deterministic wallets also enable hierarchical key generation, supporting organized management of multiple addresses and improved privacy through unique addresses for each transaction.
Limitations of Non-Deterministic Wallets
Non-deterministic wallets suffer from limited backup and recovery options since each private key is generated and stored independently, making it difficult to restore access if keys are lost. Their lack of hierarchical key derivation results in inefficient key management and increased vulnerability to security breaches. Unlike deterministic wallets that use a single seed for all keys, non-deterministic wallets require multiple backups, increasing the risk of missing critical private keys necessary for accessing funds.
Future Trends in Wallet Technology
Deterministic wallets, relying on a single seed to generate multiple private keys, enable streamlined backup and recovery, positioning them as the foundation for future wallet innovations. Non-deterministic wallets, generating keys independently, offer enhanced security but pose challenges in scalability and management, which limits their adoption in evolving digital asset ecosystems. Emerging trends favor hybrid models that integrate deterministic frameworks with advanced cryptographic protocols, such as threshold signatures and quantum-resistant algorithms, to address security, usability, and interoperability in next-generation digital wallets.
Important Terms
Hierarchical Deterministic (HD) Wallet
Hierarchical Deterministic (HD) Wallets generate a tree of cryptographic keys from a single seed for improved backup and security, unlike Non-Deterministic Wallets that create random, unrelated keys without hierarchical structure.
Seed Phrase
A seed phrase generates all private keys in deterministic wallets, enabling easy backup and recovery, whereas non-deterministic wallets use random keys without a seed phrase, complicating restoration.
Key Derivation Path
Key derivation paths enable structured and repeatable key generation in deterministic wallets, unlike non-deterministic wallets which generate independent, unrelated keys without a standardized hierarchy.
BIP32
BIP32 defines a standard for hierarchical deterministic (HD) wallets, enabling the generation of a tree of key pairs from a single seed, which enhances security and simplifies backup processes. Non-deterministic wallets generate keys randomly and independently, requiring separate backups for each key, making them less efficient compared to deterministic wallets that allow recovery of all child keys from one master seed.
BIP44
BIP44 defines a standard for hierarchical deterministic (HD) wallets, enabling the generation of a tree of key pairs from a single seed, facilitating organized and secure multi-cryptocurrency management. In contrast, non-deterministic wallets generate keys independently without a fixed derivation path, making backup and recovery less straightforward compared to BIP44-compliant deterministic wallets.
Single Key Wallet
A Single Key Wallet is a non-deterministic wallet relying on a single private key for transactions, unlike deterministic wallets that generate multiple keys from a seed phrase.
Extended Public Key (xPub)
Extended Public Keys (xPubs) enable deterministic wallets to generate multiple public addresses from a single key, enhancing security and convenience compared to non-deterministic wallets that require storing separate keys for each address.
Mnemonic Code
Mnemonic code generates a human-readable seed phrase that securely derives deterministic wallets by enabling reproducible key generation, unlike non-deterministic wallets which create random keys without a recovery phrase.
Random Key Generation
Random key generation produces unique private keys for non-deterministic wallets, whereas deterministic wallets derive keys from a single seed, enabling easier backup and recovery.
Address Gap Limit
Address gap limit defines the maximum number of unused addresses generated by deterministic wallets before they stop creating new addresses, ensuring efficient key management and avoiding address bloat. Non-deterministic wallets lack a predefined address generation structure, making gap limit irrelevant and resulting in less predictable address management.
Deterministic Wallet vs Non-Deterministic Wallet Infographic
 moneydif.com
moneydif.com