A Sybil attack in cryptocurrency involves creating numerous fake identities to gain disproportionate influence over a network, undermining its trust and security. In contrast, a 51% attack occurs when a single entity or group controls the majority of the network's mining power, enabling double-spending and transaction manipulation. Both attacks exploit consensus mechanisms but target different aspects of network control and trust.
Table of Comparison
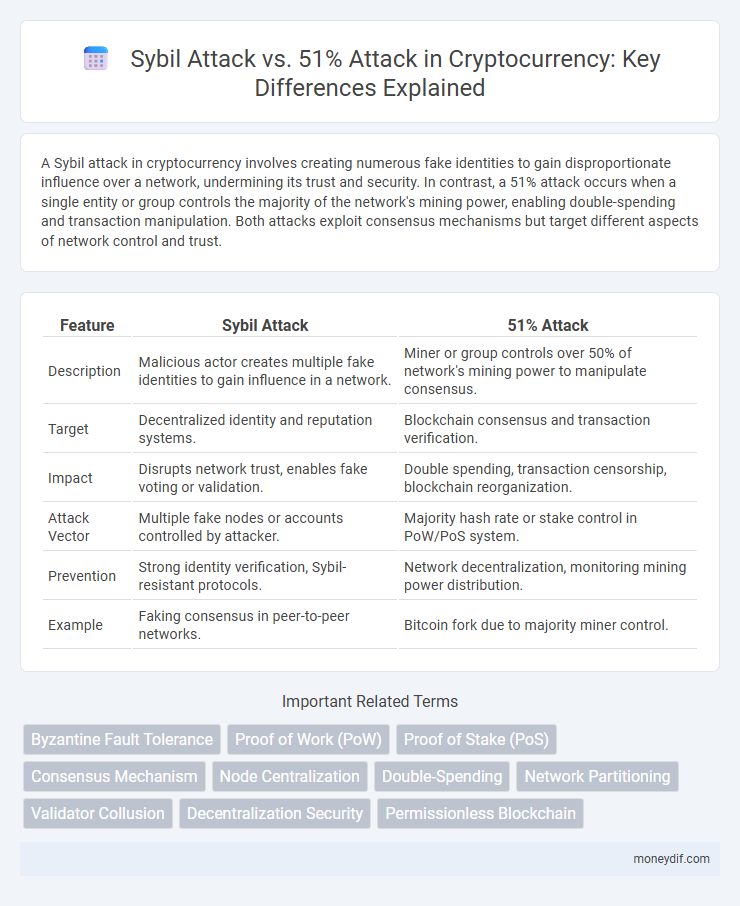
| Feature | Sybil Attack | 51% Attack |
|---|---|---|
| Description | Malicious actor creates multiple fake identities to gain influence in a network. | Miner or group controls over 50% of network's mining power to manipulate consensus. |
| Target | Decentralized identity and reputation systems. | Blockchain consensus and transaction verification. |
| Impact | Disrupts network trust, enables fake voting or validation. | Double spending, transaction censorship, blockchain reorganization. |
| Attack Vector | Multiple fake nodes or accounts controlled by attacker. | Majority hash rate or stake control in PoW/PoS system. |
| Prevention | Strong identity verification, Sybil-resistant protocols. | Network decentralization, monitoring mining power distribution. |
| Example | Faking consensus in peer-to-peer networks. | Bitcoin fork due to majority miner control. |
Understanding Sybil Attacks in Cryptocurrency
Sybil attacks in cryptocurrency involve an adversary creating multiple fake identities to gain disproportionate influence on a network, undermining trust and consensus mechanisms. Unlike 51% attacks that require controlling the majority of mining power to manipulate blockchain transactions, Sybil attacks exploit network vulnerabilities by overwhelming nodes with falsified identities. Effective defense against Sybil attacks includes robust identity verification, stake-based consensus algorithms, and limiting influence per identity to maintain decentralized integrity.
What is a 51% Attack?
A 51% attack occurs when a single entity or group controls over half of a blockchain network's mining power, allowing them to manipulate transaction validation and double-spend coins. This majority control undermines the network's consensus mechanism, enabling the attacker to prevent new transactions from gaining confirmations or to reverse completed transactions. Unlike Sybil attacks, which exploit network identities, 51% attacks specifically target mining power dominance to disrupt blockchain integrity.
Key Differences Between Sybil and 51% Attacks
Sybil attacks manipulate a blockchain network by creating numerous fake identities to gain disproportionate influence over consensus processes, whereas 51% attacks require control of over half the network's mining or staking power to dominate block validation. Sybil attacks exploit network-level vulnerabilities through identity fraud, while 51% attacks directly threaten blockchain security by enabling double-spending and transaction censorship. The core difference lies in Sybil attacks targeting identity systems, and 51% attacks focusing on computational or staking power concentration.
How Sybil Attacks Threaten Blockchain Security
Sybil attacks threaten blockchain security by allowing a malicious actor to create multiple fake identities or nodes, overwhelming the network's consensus mechanism and disrupting transaction verification. Unlike 51% attacks that require controlling the majority of computational power, Sybil attacks exploit network trust assumptions, enabling attackers to manipulate voting systems or degrade network performance without significant resource expenditure. Effective countermeasures include robust identity verification protocols, reputation systems, and resource-based constraints to prevent the proliferation of fake nodes in decentralized networks.
The Impact of 51% Attacks on Network Consensus
A 51% attack compromises network consensus by enabling an attacker controlling over half of the network's mining power to double-spend coins and censor transactions, undermining blockchain integrity. This centralization of control disrupts the decentralized trust model critical to blockchain security, causing potential loss of user funds and reduced network credibility. Unlike Sybil attacks, which rely on fake identities, 51% attacks directly manipulate the consensus mechanism through computational dominance.
Real-World Examples of Sybil Attacks
Sybil attacks manipulate peer-to-peer networks by creating multiple fake identities, as seen in Ethereum's early testnet disruptions where attackers overwhelmed nodes with bogus connections. Unlike 51% attacks that require majority mining power to rewrite blockchain history, Sybil attacks exploit network-level trust mechanisms without controlling consensus. Real-world occurrences highlight vulnerabilities in decentralized systems, emphasizing the need for robust identity verification to safeguard blockchain integrity.
Notable Cases of 51% Attacks in Crypto History
Notable cases of 51% attacks in crypto history include the 2018 Bitcoin Gold attack, where hackers reorganized the blockchain and double-spent over $18 million. Ethereum Classic suffered multiple 51% attacks in 2020, causing network instability and loss of investor confidence. These incidents highlight vulnerabilities in proof-of-work blockchains with relatively low hash rates, emphasizing the need for enhanced network security measures.
Prevention Strategies for Sybil Attacks
Sybil attacks in cryptocurrency networks can be mitigated using identity verification mechanisms such as Proof of Work (PoW) or Proof of Stake (PoS), which limit the influence of fake nodes by requiring resource investment. Network-level defenses include employing reputation systems and node authentication protocols to ensure that each node corresponds to a unique and legitimate participant. These prevention strategies differ from 51% attacks, which are thwarted primarily through distributed consensus and economic incentives rather than identity validation.
Defense Mechanisms Against 51% Attacks
Defense mechanisms against 51% attacks in cryptocurrency networks primarily involve improving decentralization and implementing robust consensus algorithms such as Proof of Stake (PoS) or delegated Proof of Stake (dPoS). Network protocols can incorporate checkpointing and finality gadgets to reduce the risk of chain reorganization caused by majority hash rate control. Additionally, economic disincentives, like slashing conditions in PoS, penalize malicious actors who attempt to manipulate the blockchain through majority attacks.
Sybil Attack vs 51% Attack: Which is More Dangerous?
A Sybil attack involves an adversary generating numerous fake identities to gain disproportionate influence in a network, undermining trust and consensus mechanisms. In contrast, a 51% attack requires controlling the majority of a blockchain's hashing power, enabling attackers to manipulate transactions and double-spend coins. While both threaten decentralization, a 51% attack poses a more immediate risk to blockchain integrity and financial security due to its ability to directly alter transaction history.
Important Terms
Byzantine Fault Tolerance
Byzantine Fault Tolerance (BFT) ensures consensus in distributed systems despite malicious or faulty nodes, effectively mitigating threats like Sybil attacks where an adversary creates multiple fake identities to gain disproportionate influence. In contrast, 51% attacks exploit majority control over consensus mechanisms, but BFT protocols strengthen network resilience by requiring agreement from a significant fraction of honest nodes, preventing single-entity dominance.
Proof of Work (PoW)
Proof of Work (PoW) secures blockchain networks by requiring computational effort to validate transactions, effectively mitigating Sybil attacks where adversaries create multiple fake identities to gain disproportionate influence. However, PoW remains vulnerable to 51% attacks, where a single malicious entity controlling the majority of the network's hashing power can manipulate transaction ordering and double-spend coins.
Proof of Stake (PoS)
Proof of Stake (PoS) secures blockchain networks by requiring validators to lock up a significant amount of cryptocurrency as collateral, reducing the risk of Sybil attacks where attackers create multiple fake identities to gain disproportionate influence. Unlike Proof of Work, PoS mitigates 51% attacks by economically disincentivizing control over the majority stake, making it costly and impractical for attackers to dominate the network consensus.
Consensus Mechanism
A consensus mechanism secures blockchain networks by validating transactions and preventing malicious activities like Sybil attacks, where an attacker creates numerous fake identities to gain influence. It also defends against 51% attacks, where a single entity controls the majority of network hash power, potentially enabling double spending or transaction censorship.
Node Centralization
Node centralization increases vulnerability to Sybil attacks by enabling a single entity to control multiple nodes and manipulate consensus processes; this concentration of power can escalate into a 51% attack where the attacker gains majority control over the network's hashing power or stake, allowing them to double-spend coins or censor transactions. Decentralized node distribution mitigates these risks by ensuring no single actor can dominate consensus validation or network security mechanisms.
Double-Spending
Double-spending exploits blockchain vulnerabilities by allowing malicious actors to reverse transactions, with Sybil attacks flooding the network with fake identities to influence consensus, while 51% attacks gain majority control of mining power to rewrite transaction history. Defenses against double-spending focus on network decentralization, proof-of-work difficulty adjustments, and robust node identity verification to mitigate Sybil and majority control threats.
Network Partitioning
Network partitioning in blockchain systems can isolate nodes, enabling Sybil attacks by allowing adversaries to create numerous fake identities within a fragmented segment, undermining consensus. In contrast, a 51% attack requires control of the majority computing power, exploiting network control rather than identity manipulation.
Validator Collusion
Validator collusion occurs when multiple validators coordinate to manipulate consensus, potentially leading to a Sybil attack where a single entity controls numerous validator identities to gain disproportionate influence. This contrasts with a 51% attack, which requires controlling a majority of the network's total staking power rather than merely a majority of validator nodes.
Decentralization Security
Decentralization security crucially mitigates vulnerabilities like Sybil attacks, where multiple fake identities disrupt network consensus, and 51% attacks, where a single entity controls majority hashing power to manipulate blockchain transactions. Robust distributed consensus algorithms and identity verification mechanisms strengthen network integrity, preventing dominance by malicious actors in decentralized systems.
Permissionless Blockchain
Permissionless blockchains, designed to operate without centralized control, are vulnerable to Sybil attacks where an adversary creates multiple fake identities to gain disproportionate influence over the network. In contrast, a 51% attack requires controlling a majority of the network's mining power or stake, allowing an attacker to manipulate transaction validation and potentially double-spend coins.
Sybil Attack vs 51% Attack Infographic
 moneydif.com
moneydif.com