Whitelist and blacklist are crucial mechanisms in cryptocurrency security, where whitelisting allows only approved addresses to access specific functions, enhancing transaction safety. Blacklisting blocks suspicious or malicious addresses, preventing fraudulent activities and protecting users' assets. Employing both strategies optimizes network integrity by balancing accessibility with risk management.
Table of Comparison
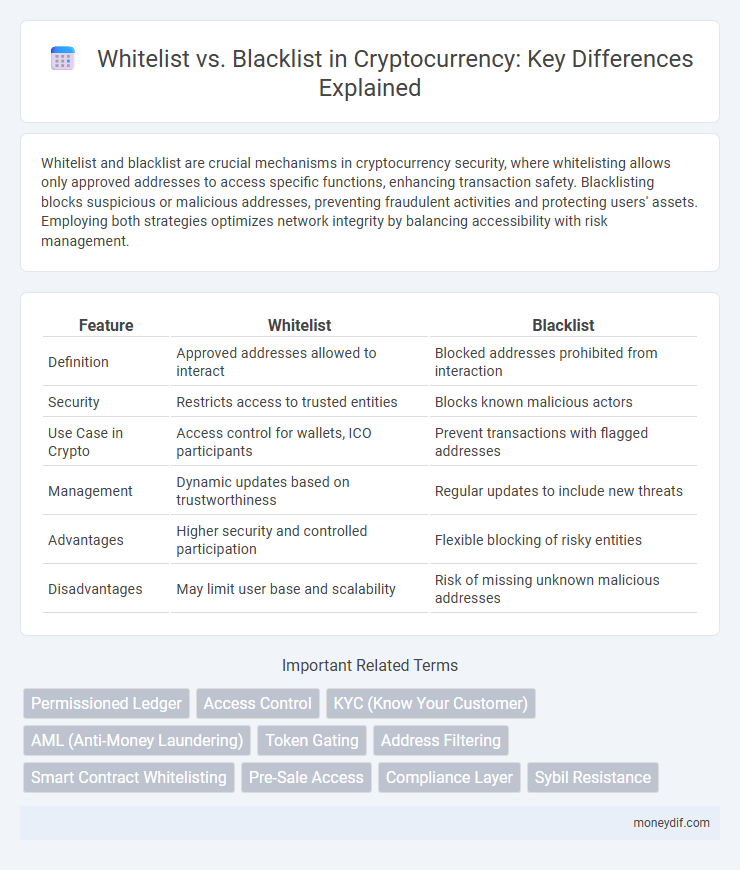
| Feature | Whitelist | Blacklist |
|---|---|---|
| Definition | Approved addresses allowed to interact | Blocked addresses prohibited from interaction |
| Security | Restricts access to trusted entities | Blocks known malicious actors |
| Use Case in Crypto | Access control for wallets, ICO participants | Prevent transactions with flagged addresses |
| Management | Dynamic updates based on trustworthiness | Regular updates to include new threats |
| Advantages | Higher security and controlled participation | Flexible blocking of risky entities |
| Disadvantages | May limit user base and scalability | Risk of missing unknown malicious addresses |
Introduction to Whitelisting and Blacklisting in Cryptocurrency
Whitelisting in cryptocurrency involves creating a list of approved wallet addresses or entities allowed to participate in transactions or token sales, enhancing security by restricting access to trusted participants only. Blacklisting, on the other hand, blocks specific addresses or entities from engaging in transactions due to fraud, regulatory compliance, or suspicious activity. Both mechanisms are critical for safeguarding blockchain ecosystems, preventing unauthorized access, and ensuring compliance with AML (Anti-Money Laundering) and KYC (Know Your Customer) regulations.
Defining Whitelist: Meaning and Applications
A whitelist in cryptocurrency refers to a pre-approved list of wallets or users allowed to participate in specific activities, such as token sales or access to exclusive features. It enhances security by restricting access to trusted participants and reduces the risk of fraud or unauthorized transactions. Common applications include Initial Coin Offerings (ICOs), exclusive airdrops, and advanced platform functionalities that require verified users.
Understanding Blacklist in Crypto Ecosystems
A blacklist in cryptocurrency ecosystems refers to a list of addresses or accounts that are blocked or restricted from participating in transactions due to suspicious or malicious activity, such as fraud or money laundering. Blockchain networks and exchanges use blacklists to enhance security and comply with regulatory requirements by preventing flagged entities from transferring or receiving digital assets. Understanding how blacklists function helps users recognize the importance of compliance measures and the risks associated with interacting with potentially compromised addresses.
Whitelist vs Blacklist: Key Differences
Whitelist and blacklist are contrasting approaches in cryptocurrency security and access control. A whitelist permits only pre-approved addresses or users, enhancing security by restricting participation to trusted entities, whereas a blacklist blocks specific addresses or users known for malicious activity. Whitelisting provides proactive protection by defaulting to denial, while blacklisting is reactive, relying on identifying and banning threats after they occur.
How Whitelists Benefit Crypto Projects and Investors
Whitelists enhance security by allowing only verified users to participate in token sales, reducing the risk of fraud and malicious attacks in cryptocurrency projects. They improve compliance with regulatory requirements, ensuring that investors meet specific criteria and minimizing legal complications. By fostering trust and transparency, whitelists attract serious investors, promote a healthier token economy, and drive long-term project success.
The Role of Blacklists in Enhancing Security
Blacklists play a crucial role in cryptocurrency security by preventing transactions and addresses associated with fraud, theft, and money laundering from participating in the network. By actively blocking suspicious wallets and malicious actors, blacklists mitigate risks and enhance the overall trustworthiness of blockchain platforms. This security measure helps protect users' assets and maintain regulatory compliance across decentralized exchanges and wallets.
Whitelisting in ICOs, Token Sales, and Airdrops
Whitelisting in ICOs, token sales, and airdrops ensures that only pre-approved, verified participants can access token distribution, enhancing compliance with KYC and AML regulations. This process reduces fraud and unauthorized transactions by requiring users to submit identification and wallet details before participation. Whitelisting builds investor trust and secures fundraising events by limiting access to legitimate contributors.
Regulatory Perspectives on Whitelists and Blacklists
Regulators use whitelists and blacklists to enforce compliance and prevent illicit activities in cryptocurrency markets, with whitelists allowing known, verified entities to operate while blacklists restrict access to suspicious or banned addresses. Whitelists support anti-money laundering (AML) and know-your-customer (KYC) frameworks by ensuring only approved participants engage in transactions. Blacklists help mitigate risks associated with fraud, terrorism financing, and sanctions violations by blocking transactions involving flagged wallets or entities.
Case Studies: Whitelisting and Blacklisting in Action
Whitelisting in cryptocurrency ensures secure transactions by allowing only pre-approved addresses to interact with a smart contract, exemplified by Ethereum's decentralized finance platforms that prevent unauthorized access to funds. Blacklisting, conversely, blocks specific addresses associated with fraudulent activities, such as exchanges blacklisting wallets linked to hacks or regulatory violations, seen in Bitcoin exchanges implementing compliance measures. Case studies from projects like Binance and Compound showcase how whitelisting enhances user trust while blacklisting enforces security and regulatory adherence.
Future Trends: Evolution of Access Controls in Crypto
Whitelist and blacklist access controls are evolving to address increasing demands for security and regulatory compliance in cryptocurrency. Emerging trends include dynamic, AI-driven whitelist systems that adapt to real-time user behavior and decentralized identity verification protocols to minimize reliance on traditional blacklists. Future mechanisms aim to balance privacy with transparency, enhancing trust and scalability in blockchain environments.
Important Terms
Permissioned Ledger
A permissioned ledger restricts network access to approved participants, often managed through whitelist controls that explicitly grant transaction and validation rights. In contrast, blacklist mechanisms block specific entities or addresses, but whitelisting enhances security and compliance by pre-approving trusted nodes in blockchain environments.
Access Control
Access control utilizes whitelist and blacklist methodologies to regulate user permissions, where whitelisting explicitly allows approved entities access while blacklisting blocks identified unauthorized users. Implementing a whitelist approach enhances security by defaulting to deny access unless explicitly permitted, whereas blacklisting offers broader access but requires continuous updates to block new threats.
KYC (Know Your Customer)
KYC (Know Your Customer) processes enhance financial security by verifying customer identities to prevent fraud, with whitelist and blacklist systems playing pivotal roles: whitelists include approved, verified customers authorized for transactions, while blacklists contain individuals flagged for suspicious or illegal activities. Implementing KYC-driven whitelists streamlines compliant customer onboarding, whereas blacklists effectively block high-risk entities to mitigate money laundering and terrorist financing risks.
AML (Anti-Money Laundering)
AML (Anti-Money Laundering) efforts rely heavily on the effective use of whitelists and blacklists to manage transactional risk; whitelists ensure trusted entities bypass routine scrutiny, while blacklists block transactions involving suspicious or sanctioned parties. Integrating dynamic blacklists updated with global watchlists and regulatory sanctions enhances the detection of illicit activities, whereas maintaining accurate whitelists reduces false positives and streamlines compliance processes.
Token Gating
Token gating employs whitelist and blacklist mechanisms to control user access based on ownership of specific digital tokens, where whitelists grant permissions to verified holders while blacklists restrict malicious or unauthorized users. This approach enhances security and exclusivity in decentralized applications, NFT communities, and blockchain-based platforms by leveraging token validation and access management.
Address Filtering
Address filtering enhances network security by controlling access through whitelists, which explicitly allow trusted IP addresses, while blacklists block known malicious or unauthorized ones; whitelisting offers stricter control by permitting only listed addresses, whereas blacklisting provides broader access but prevents access from harmful sources. Effective deployment of address filtering depends on maintaining updated lists and balancing security needs with network usability to prevent unauthorized access and reduce false positives.
Smart Contract Whitelisting
Smart contract whitelisting enhances blockchain security by allowing only pre-approved addresses to execute specific functions, reducing the risk of unauthorized access and exploit attempts. Unlike blacklisting, which blocks known malicious actors after detection, whitelisting proactively restricts interactions to trusted entities, ensuring a more controlled and secure smart contract environment.
Pre-Sale Access
Pre-sale access often leverages whitelist protocols to grant privileged users early entry to exclusive offers, enhancing user trust and project credibility by ensuring only verified participants can join. In contrast, blacklist methods explicitly prohibit certain addresses, optimizing security by blocking potential fraudsters but risking exclusion errors that may reduce overall engagement.
Compliance Layer
The Compliance Layer enforces security policies by integrating whitelist and blacklist mechanisms, where whitelists allow pre-approved entities access while blacklists block known threats, ensuring regulatory adherence and minimizing unauthorized activity. Effective management within this layer leverages dynamic updates to these lists, optimizing risk mitigation and maintaining compliance with industry standards such as GDPR and HIPAA.
Sybil Resistance
Sybil resistance enhances network security by preventing fake or duplicate identities, commonly addressed through whitelist and blacklist mechanisms; whitelisting permits only verified entities to participate, ensuring trusted access, while blacklisting blocks known malicious actors to reduce fraudulent activity. Implementing these strategies improves consensus protocols and fraud detection, crucial for maintaining integrity in decentralized systems.
Whitelist vs Blacklist Infographic
 moneydif.com
moneydif.com