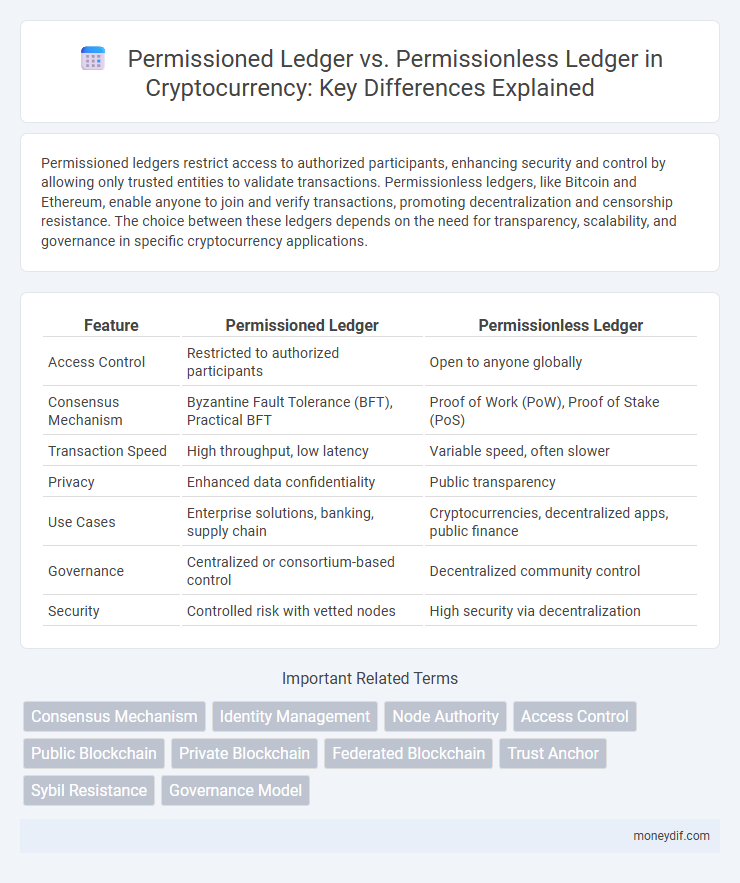
Permissioned ledgers restrict access to authorized participants, enhancing security and control by allowing only trusted entities to validate transactions. Permissionless ledgers, like Bitcoin and Ethereum, enable anyone to join and verify transactions, promoting decentralization and censorship resistance. The choice between these ledgers depends on the need for transparency, scalability, and governance in specific cryptocurrency applications.
Table of Comparison
| Feature | Permissioned Ledger | Permissionless Ledger |
|---|---|---|
| Access Control | Restricted to authorized participants | Open to anyone globally |
| Consensus Mechanism | Byzantine Fault Tolerance (BFT), Practical BFT | Proof of Work (PoW), Proof of Stake (PoS) |
| Transaction Speed | High throughput, low latency | Variable speed, often slower |
| Privacy | Enhanced data confidentiality | Public transparency |
| Use Cases | Enterprise solutions, banking, supply chain | Cryptocurrencies, decentralized apps, public finance |
| Governance | Centralized or consortium-based control | Decentralized community control |
| Security | Controlled risk with vetted nodes | High security via decentralization |
Understanding Permissioned and Permissionless Ledgers
Permissioned ledgers restrict access and transaction validation to authorized participants, enhancing privacy and control ideal for enterprise use cases. Permissionless ledgers, such as Bitcoin and Ethereum, allow anyone to join, validate transactions, and participate in consensus, promoting decentralization and transparency. Understanding these distinctions is crucial for selecting the appropriate blockchain type based on security, scalability, and governance needs.
Key Differences Between Permissioned and Permissionless Ledgers
Permissioned ledgers restrict access to authorized participants, enabling greater control, streamlined compliance, and faster transaction processing, ideal for enterprises requiring privacy and regulatory adherence. Permissionless ledgers, such as Bitcoin and Ethereum, allow anyone to join and validate transactions, promoting decentralization, transparency, and censorship resistance. Key differences include governance models, scalability, consensus mechanisms, and user privacy, with permissioned ledgers emphasizing trust among known entities while permissionless ledgers rely on cryptographic proofs and economic incentives.
Governance Models in Blockchain: Permissioned vs. Permissionless
Permissioned ledgers feature centralized governance where a defined group of validators controls access and transaction validation, enhancing security and compliance for enterprise use cases. Permissionless ledgers operate on decentralized governance, allowing anyone to participate in consensus mechanisms like proof-of-work or proof-of-stake, fostering transparency and censorship resistance. The governance model impacts scalability, trust assumptions, and regulatory alignment, influencing blockchain adoption across various industries.
Security Implications: Permissioned vs. Permissionless Ledgers
Permissioned ledgers restrict network access to authorized participants, enhancing security through controlled validation and reduced risk of malicious actors, making them ideal for enterprise use cases requiring compliance and privacy. Permissionless ledgers allow anyone to join and validate transactions, providing decentralization and censorship resistance but increasing vulnerability to attacks such as 51% attacks and Sybil attacks. The choice between permissioned and permissionless ledgers hinges on balancing security, trust, and transparency requirements in cryptocurrency ecosystems.
Scalability and Performance Comparison
Permissioned ledgers typically offer higher scalability and performance due to controlled access and optimized consensus algorithms, allowing faster transaction processing and lower latency compared to permissionless ledgers. Permissionless ledgers rely on decentralized consensus mechanisms like Proof of Work or Proof of Stake, which can limit throughput and increase confirmation times due to network-wide validation. Enterprises prioritize permissioned ledgers for applications requiring high transaction speed, deterministic finality, and greater control over network participants.
Use Cases: Where Permissioned and Permissionless Ledgers Excel
Permissioned ledgers excel in enterprise use cases requiring enhanced security and regulatory compliance, such as supply chain management and interbank settlements, by restricting access to verified participants. Permissionless ledgers, like Bitcoin and Ethereum, support decentralized finance (DeFi) and public tokenization, enabling open participation and censorship resistance. Both ledger types leverage blockchain technology but differ fundamentally in governance models and access control, tailoring their utility to specific industry needs.
Consensus Mechanisms: Contrasting Permissioned and Permissionless Networks
Permissioned ledgers use consensus mechanisms like Practical Byzantine Fault Tolerance (PBFT) to enhance transaction speed and reduce energy consumption by limiting validation to a known set of participants. Permissionless ledgers rely on consensus algorithms such as Proof of Work (PoW) or Proof of Stake (PoS), enabling open participation but often resulting in higher computational costs and longer confirmation times. These distinct consensus models reflect trade-offs between scalability, security, and decentralization in blockchain networks.
Regulatory Compliance in Different Ledger Types
Permissioned ledgers offer enhanced regulatory compliance by enabling controlled access, participant verification, and transparent audit trails crucial for meeting legal standards such as KYC and AML. In contrast, permissionless ledgers provide open, decentralized networks where anonymity can challenge regulatory enforcement and complicate compliance measures. Regulatory bodies often favor permissioned systems for their ability to enforce accountability and ensure transaction traceability within cryptocurrency ecosystems.
Privacy Features in Permissioned vs. Permissionless Ledgers
Permissioned ledgers enhance privacy by restricting access to authorized participants and implementing granular permission controls, ensuring sensitive transaction data remains confidential within a trusted network. In contrast, permissionless ledgers operate on a public blockchain where transaction data is transparent and accessible to all participants, prioritizing decentralization and openness over privacy. Advanced cryptographic techniques like zero-knowledge proofs and ring signatures are often required on permissionless platforms to achieve privacy without compromising transparency.
Choosing the Right Ledger Type for Your Project
Choosing the right ledger type for your cryptocurrency project depends on factors such as security requirements, scalability, and user accessibility. Permissioned ledgers offer controlled access, enhanced privacy, and faster transaction speeds, making them suitable for enterprise applications and regulatory compliance. Permissionless ledgers provide decentralized trust, transparency, and wider network participation, ideal for open financial systems and public blockchain projects.
Important Terms
Consensus Mechanism
Consensus mechanisms in permissioned ledgers rely on predefined validators, enhancing transaction speed and security through restricted network participation, while permissionless ledgers utilize open, decentralized consensus algorithms like Proof of Work or Proof of Stake, prioritizing transparency and censorship resistance despite higher computational costs. The choice between these mechanisms impacts scalability, trust models, and governance structures in distributed ledger technologies.
Identity Management
Identity management in permissioned ledgers ensures robust access control by verifying participants through centralized or consortium-based authorities, enhancing security and compliance. In contrast, permissionless ledgers offer decentralized identity validation without trusted intermediaries, prioritizing anonymity and open participation but with less granular access control.
Node Authority
Node Authority determines the level of control and validation power each node possesses within a blockchain network, varying significantly between permissioned and permissionless ledgers. Permissioned ledgers restrict Node Authority to vetted participants with predefined access rights, enhancing security and compliance, while permissionless ledgers grant open, decentralized Node Authority, allowing any participant to validate transactions and maintain consensus.
Access Control
Access control in permissioned ledgers enforces strict identity verification and role-based permissions to regulate participant actions, ensuring data privacy and compliance within a trusted network. In contrast, permissionless ledgers allow open access and control through consensus mechanisms like proof-of-work, prioritizing decentralization and transparency over restrictive access rights.
Public Blockchain
Public blockchains operate as permissionless ledgers, allowing anyone to join, validate transactions, and participate in consensus mechanisms without restrictions, ensuring decentralization and transparency. Permissioned ledgers restrict access to authorized participants, combining controlled governance with blockchain's immutability, suitable for enterprise use cases requiring privacy and regulatory compliance.
Private Blockchain
Private blockchain operates as a permissioned ledger where access is restricted to verified participants, enabling enhanced security and control over data sharing. Unlike permissionless ledgers that allow open participation and consensus, private blockchains support faster transactions and greater privacy by limiting validation rights to trusted nodes.
Federated Blockchain
Federated blockchain, also known as a consortium blockchain, operates as a permissioned ledger where only selected participants have the authority to validate transactions, ensuring higher control and privacy compared to permissionless ledgers like Bitcoin or Ethereum that allow open access to any user for transaction validation. This structure enhances scalability and regulatory compliance while maintaining decentralization among trusted members rather than a fully open network.
Trust Anchor
A Trust Anchor in permissioned ledgers serves as a centralized authority that validates identities and controls access, enhancing security and compliance. In contrast, permissionless ledgers rely on decentralized consensus mechanisms without a Trust Anchor, prioritizing openness and trust through cryptographic protocols.
Sybil Resistance
Sybil resistance is a critical security feature in permissionless ledgers, utilizing mechanisms such as proof-of-work or proof-of-stake to prevent malicious entities from creating multiple fake identities and gaining disproportionate control. In contrast, permissioned ledgers rely on identity verification and controlled access among trusted parties, reducing the need for complex Sybil resistance protocols by restricting participation to authorized nodes.
Governance Model
Governance models in permissioned ledgers rely on a defined group of authorized participants to validate transactions and enforce rules, enhancing control and compliance in enterprise blockchains. Permissionless ledgers use decentralized consensus mechanisms, allowing any participant to join and validate transactions, fostering transparency and censorship resistance at the cost of slower transaction speeds.
permissioned ledger vs permissionless ledger Infographic
 moneydif.com
moneydif.com