A Dusting Attack involves sending tiny amounts of cryptocurrency to multiple wallets to trace transaction patterns and de-anonymize users, posing privacy risks. Replay Attacks exploit the similarity between transactions on different blockchains, allowing malicious actors to duplicate a valid transaction across multiple networks. Understanding these attack vectors is crucial for enhancing wallet security and protecting digital assets.
Table of Comparison
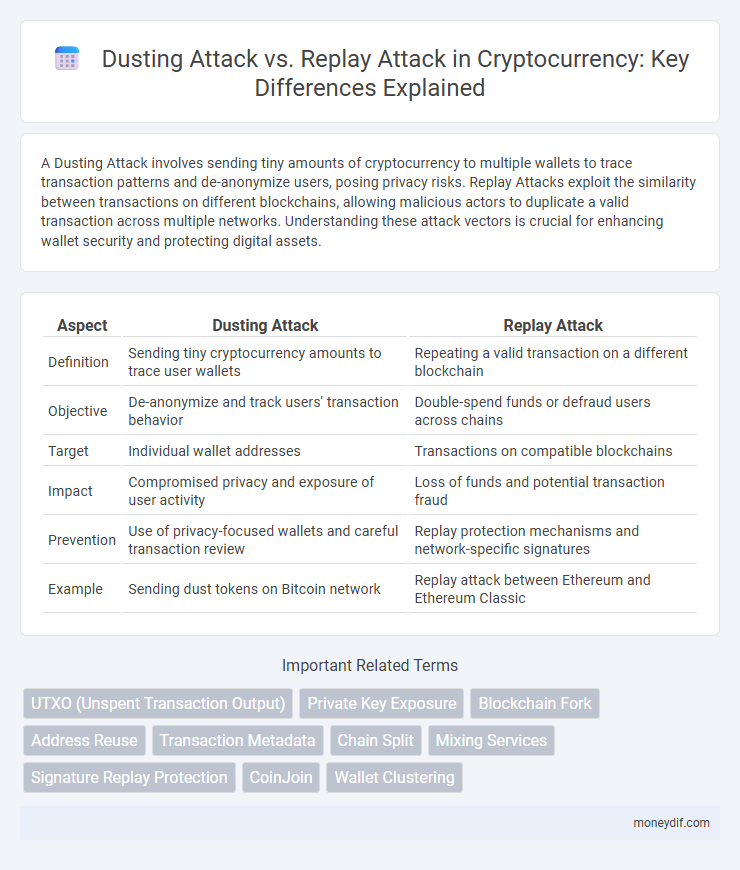
| Aspect | Dusting Attack | Replay Attack |
|---|---|---|
| Definition | Sending tiny cryptocurrency amounts to trace user wallets | Repeating a valid transaction on a different blockchain |
| Objective | De-anonymize and track users' transaction behavior | Double-spend funds or defraud users across chains |
| Target | Individual wallet addresses | Transactions on compatible blockchains |
| Impact | Compromised privacy and exposure of user activity | Loss of funds and potential transaction fraud |
| Prevention | Use of privacy-focused wallets and careful transaction review | Replay protection mechanisms and network-specific signatures |
| Example | Sending dust tokens on Bitcoin network | Replay attack between Ethereum and Ethereum Classic |
Introduction to Dusting Attack and Replay Attack
Dusting attacks involve sending tiny amounts of cryptocurrency to multiple wallets to trace and deanonymize users by analyzing transaction patterns. Replay attacks exploit transaction data by copying valid transactions from one blockchain and broadcasting them on another, causing unauthorized transfers. Both attack types threaten user privacy and asset security across decentralized networks.
Defining Dusting Attack in Cryptocurrency
A dusting attack in cryptocurrency involves sending tiny amounts of coins, known as "dust," to multiple wallets to trace and analyze user behavior on the blockchain. This technique helps attackers link addresses and deanonymize cryptocurrency users by tracking the movement of dust transactions through various wallets. Unlike replay attacks that duplicate transactions across networks, dusting attacks target privacy and user identification rather than transaction validity.
What is a Replay Attack?
A replay attack occurs when a malicious actor intercepts and fraudulently reuses a valid cryptocurrency transaction to duplicate the transfer or double-spend assets. This type of attack exploits the lack of replay protection between blockchain networks, especially after hard forks, allowing the transaction to be replicated on multiple chains. Implementing replay protection through unique transaction signatures or chain identifiers is critical to preventing such attacks and safeguarding user funds.
Key Differences: Dusting Attack vs Replay Attack
Dusting attacks involve sending tiny amounts of cryptocurrency to numerous wallets to trace transaction patterns and de-anonymize users, whereas replay attacks exploit a transaction made on one blockchain to execute the same transaction on another, often after a chain split or fork. Dusting targets privacy by linking addresses, while replay attacks target transaction validity and security across chains. Understanding their operational mechanisms helps enhance wallet security and blockchain protocol design.
How Dusting Attacks Compromise User Privacy
Dusting attacks compromise user privacy by sending tiny amounts of cryptocurrency to multiple wallets, enabling attackers to track and analyze transaction patterns across addresses and ultimately link them to real-world identities. These micro-transactions correlate wallet activities, breaking users' anonymity and exposing their financial behavior. Unlike replay attacks that exploit transaction replays across networks, dusting attacks specifically target privacy through data aggregation and sophisticated blockchain analysis.
Replay Attacks: Impact on Blockchain Security
Replay attacks exploit vulnerabilities in blockchain networks by repeating valid transaction data to fraudulently transfer assets, compromising transaction integrity and user security. These attacks undermine trust in blockchain systems by enabling attackers to duplicate transactions across parallel chains or forks, leading to potential double-spending and financial loss. Effective countermeasures include replay protection mechanisms such as chain ID differentiation and transaction signature enhancements to safeguard blockchain security.
Real-World Cases: Dusting and Replay Attacks
Dusting attacks have targeted Bitcoin and privacy-focused coins like Monero, where attackers send tiny amounts of cryptocurrency to wallets to trace user behavior and deanonymize transactions, as seen in incidents involving Bitcoin Dusting Campaigns in 2020. Replay attacks have notably affected Ethereum-based tokens during hard forks and chain splits, exemplified by the 2016 Ethereum and Ethereum Classic split, where identical transaction data was executed on both chains causing double-spending risks. Effective countermeasures include transaction replay protection protocols and improved wallet privacy features to mitigate these real-world vulnerabilities in cryptocurrency ecosystems.
Prevention Strategies for Dusting Attacks
Dusting attacks in cryptocurrency involve sending tiny amounts of dust to multiple wallets to trace and de-anonymize users, making privacy-focused wallets a primary defense. Implementing address reuse minimization and using mixing services or coinjoin protocols can significantly disrupt attackers' ability to link transactions. Regular wallet monitoring and employing privacy-enhancing tools such as Tor or VPNs mitigate the risk by obscuring transaction origination and wallet linkage.
Mitigation Techniques for Replay Attacks
Replay attacks in cryptocurrency can be mitigated effectively using chain replay protection techniques such as unique transaction signatures and distinct network identifiers. Implementing replay protection through protocol upgrades like Ethereum's EIP-155 or Bitcoin Cash's chain-specific rules ensures transactions on one chain are invalid on another. Wallets and exchanges also play a critical role by incorporating replay protection mechanisms to prevent duplicated transaction broadcasts across forked networks.
Future Risks and Evolving Threats in Crypto Attacks
Dusting attacks exploit tiny transaction outputs to trace user identities, posing growing privacy risks as blockchain analytics improve. Replay attacks enable fraudulent duplicate transactions across chains, threatening asset security amid increasing cross-chain interoperability. Future threats will likely combine dusting's de-anonymization capabilities with sophisticated replay techniques targeting multi-chain ecosystems, demanding advanced cryptographic defenses.
Important Terms
UTXO (Unspent Transaction Output)
UTXO (Unspent Transaction Output) serves as the fundamental element for transaction validation in blockchain networks by representing spendable cryptocurrency amounts, which attackers exploit in dusting attacks by sending minuscule amounts to trace wallet activity and compromise privacy. Replay attacks, however, manipulate identical UTXOs on different blockchain forks or chains, allowing malicious actors to duplicate transactions and steal funds unless replay protection mechanisms are implemented.
Private Key Exposure
Private key exposure significantly increases vulnerability to dusting attacks, where attackers send tiny amounts of cryptocurrency to trace wallet activity and link identities. Replay attacks exploit exposed private keys by duplicating valid transaction signatures on multiple blockchains, causing unauthorized transactions and potential financial loss.
Blockchain Fork
A blockchain fork occurs when a network splits into two separate chains due to protocol changes or disagreements, creating potential vulnerabilities exploited by dusting and replay attacks. Dusting attacks involve sending tiny amounts of cryptocurrency to many wallets to trace ownership, while replay attacks reuse valid transaction data across forked chains to fraudulently duplicate transactions.
Address Reuse
Address reuse in cryptocurrency heightens vulnerability to dusting attacks, where tiny amounts of tokens are sent to track user behavior, exposing wallet patterns, while replay attacks exploit repeated transactions on different blockchains with overlapping addresses to fraudulently duplicate transfers. Preventing address reuse enhances privacy and security by minimizing traceability and blocking malicious attempts to replicate transactions across forks or similar networks.
Transaction Metadata
Transaction metadata plays a crucial role in differentiating dusting attacks from replay attacks by encoding unique identifiers and timestamps that prevent unauthorized reuse of transaction data. In dusting attacks, metadata helps track minute, scattered cryptocurrency outputs designed to deanonymize wallets, while in replay attacks, metadata ensures that each transaction is cryptographically bound to a specific chain to avoid duplicated transactions on alternative blockchains.
Chain Split
A Chain Split occurs when a blockchain divides into two separate chains due to protocol disagreements or malicious attacks, causing transaction history divergence. Dusting Attacks exploit small, traceable transactions to deanonymize users, while Replay Attacks reuse valid transaction data across split chains, compromising transaction security and user funds.
Mixing Services
Mixing services enhance transaction privacy by obscuring the origin of funds, effectively mitigating the risks posed by replay attacks that reuse valid transaction data maliciously. While they can reduce exposure to dusting attacks--where attackers send tiny amounts of cryptocurrency to trace user activity--mixers primarily focus on breaking transaction links rather than eliminating traceable dust inputs.
Signature Replay Protection
Signature Replay Protection safeguards blockchain transactions by preventing malicious actors from reusing valid digital signatures, thereby mitigating Replay Attacks where intercepted signatures replicate unauthorized transactions. In contrast, Dusting Attacks subtly track wallet behavior through tiny transaction outputs but do not directly exploit signature reuse, highlighting the distinct security mechanisms required to counter each threat effectively.
CoinJoin
CoinJoin enhances Bitcoin transaction privacy by merging multiple users' inputs into a single transaction, obscuring the origin of funds and mitigating dusting attacks that involve sending tiny amounts of cryptocurrency to track users. While CoinJoin effectively counters dusting attacks by blending outputs, replay attacks exploit transaction records on different chains and require separate replay protection mechanisms beyond CoinJoin's scope.
Wallet Clustering
Wallet clustering techniques analyze transaction patterns and address behaviors to identify groups of cryptocurrency addresses controlled by the same entity, enhancing the detection of dusting attacks where small amounts of dust are sent to trace wallet ownership. In contrast, replay attacks exploit transaction duplication across blockchains, making wallet clustering less effective as a defense, thereby requiring additional safeguards like chain-specific signatures or replay protection mechanisms.
Dusting Attack vs Replay Attack Infographic
 moneydif.com
moneydif.com