Tokenization replaces sensitive payment data with unique identification symbols that retain essential information without exposing actual details, enhancing security during transactions. Encryption transforms payment data into a coded format that can only be decoded with a specific key, protecting the data in transit or storage from unauthorized access. Both methods are crucial for safeguarding payment information, but tokenization minimizes the risk by limiting sensitive data exposure, while encryption ensures data confidentiality during communication.
Table of Comparison
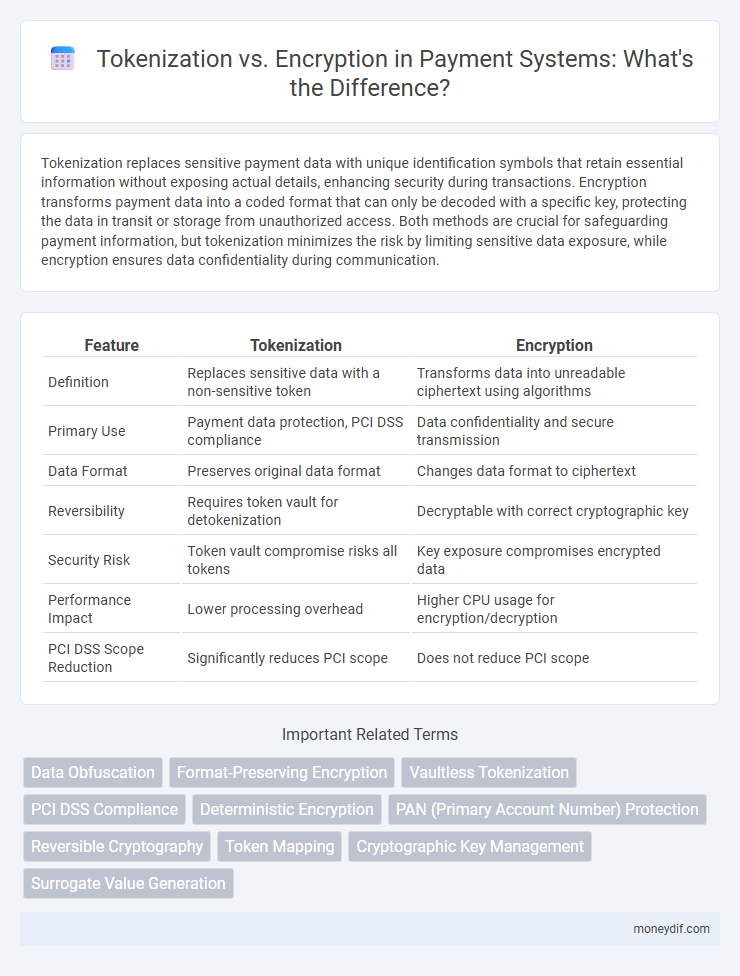
| Feature | Tokenization | Encryption |
|---|---|---|
| Definition | Replaces sensitive data with a non-sensitive token | Transforms data into unreadable ciphertext using algorithms |
| Primary Use | Payment data protection, PCI DSS compliance | Data confidentiality and secure transmission |
| Data Format | Preserves original data format | Changes data format to ciphertext |
| Reversibility | Requires token vault for detokenization | Decryptable with correct cryptographic key |
| Security Risk | Token vault compromise risks all tokens | Key exposure compromises encrypted data |
| Performance Impact | Lower processing overhead | Higher CPU usage for encryption/decryption |
| PCI DSS Scope Reduction | Significantly reduces PCI scope | Does not reduce PCI scope |
Understanding Tokenization in Payment Security
Tokenization in payment security replaces sensitive card data with unique identification symbols or tokens, significantly reducing the risk of data breaches. Unlike encryption, which scrambles data and requires decryption keys, tokenization eliminates the need to store actual card details, minimizing exposure during transactions. This method is widely adopted in PCI DSS compliance frameworks to enhance the protection of cardholder information across payment networks.
What is Encryption in Payment Processing?
Encryption in payment processing is the method of converting sensitive cardholder data into a coded format using algorithms, ensuring that information is unreadable to unauthorized parties during transmission and storage. This security measure protects data from interception and fraud by requiring a decryption key to restore the data to its original form. Payment processors rely on encryption standards such as AES and TLS to safeguard transactions and comply with PCI DSS regulations.
Core Differences Between Tokenization and Encryption
Tokenization replaces sensitive payment data with unique identification symbols or tokens that hold no exploitable value outside the specific transaction context, whereas encryption transforms data into a coded format requiring a decryption key to revert to the original information. Tokenization reduces the scope of PCI DSS compliance by avoiding the storage of actual card details, while encryption secures data in transit or at rest but still involves managing encryption keys. The core difference lies in tokenization's irreversible data substitution compared to encryption's reversible data transformation.
How Tokenization Enhances Payment Data Protection
Tokenization enhances payment data protection by replacing sensitive card information with unique, non-sensitive tokens that are useless if breached. Unlike encryption, tokens cannot be mathematically reversed to reveal original data, significantly reducing the risk of data theft during transactions. This method minimizes the scope of compliance requirements such as PCI DSS by securing payment details outside merchant systems.
The Role of Encryption in Securing Payment Transactions
Encryption secures payment transactions by converting sensitive data such as credit card numbers into unreadable ciphertext, ensuring information remains protected during transmission and storage. It employs robust algorithms like AES or RSA, which prevent unauthorized access and mitigate risks of data breaches and fraud. Encryption is critical for compliance with security standards like PCI DSS, reinforcing trust between consumers and payment systems.
Comparing Compliance Requirements: Tokenization vs Encryption
Tokenization reduces PCI DSS scope by replacing sensitive card data with non-sensitive tokens, minimizing exposure and simplifying compliance efforts. Encryption secures payment data by rendering it unreadable without decryption keys but requires managing complex key storage and rotation to meet PCI DSS standards. Tokenization often results in lower compliance costs and operational risk compared to encryption, which demands rigorous control and audit measures to ensure data protection.
Performance and Scalability: Which Solution Fits Modern Payments?
Tokenization enhances performance and scalability in modern payments by replacing sensitive card data with lightweight tokens that require less processing power and enable faster transaction speeds across high-volume environments. Encryption secures data by transforming it into complex ciphertext, but the resource-intensive process can slow down transaction throughput and strain system scalability during peak demand. Choosing tokenization supports seamless expansion and reduces latency in payment networks, making it the preferred solution for handling growing transaction volumes efficiently.
Tokenization vs Encryption: Impact on User Experience
Tokenization enhances user experience by replacing sensitive payment data with unique tokens, reducing fraud risk without compromising transaction speed or convenience. Encryption secures payment information through complex algorithms but can introduce latency and complexity during processing. Tokenization simplifies compliance requirements and improves checkout fluidity, making it a preferred method for seamless and secure payment experiences.
Choosing the Right Approach for Payment Security
Tokenization replaces sensitive payment data with non-sensitive tokens, minimizing exposure and reducing PCI DSS scope, while encryption scrambles data to prevent unauthorized access during transmission and storage. Choosing the right approach for payment security depends on the transaction environment, with tokenization preferred for reducing risk at the point of sale or in databases, and encryption essential for securing data in transit or across networks. Implementing a combination of tokenization and encryption often provides a layered defense, ensuring comprehensive protection against fraud and data breaches.
Future Trends in Payment Security: Tokenization and Encryption
Future trends in payment security emphasize the growing adoption of tokenization due to its ability to replace sensitive payment data with unique tokens, reducing fraud risks and improving compliance with PCI DSS standards. Encryption remains vital by securing data in transit and at rest, yet tokenization offers more efficient, low-latency transaction processing suitable for mobile wallets and contactless payments. The integration of tokenization with advanced encryption algorithms and biometrics is expected to define next-generation payment security frameworks, enhancing consumer trust and safeguarding against evolving cyber threats.
Important Terms
Data Obfuscation
Data obfuscation enhances security by replacing sensitive information with tokens through tokenization, which limits exposure compared to encryption that encodes data but requires complex key management and remains vulnerable if keys are compromised.
Format-Preserving Encryption
Format-Preserving Encryption (FPE) securely encrypts data while maintaining its original format, offering a seamless alternative to tokenization by enabling encrypted data to be used directly in legacy systems without altering data structure.
Vaultless Tokenization
Vaultless tokenization enhances data security by replacing sensitive information with tokens without storing the original data, unlike encryption which relies on cryptographic algorithms and key management for data protection.
PCI DSS Compliance
Tokenization enhances PCI DSS compliance by replacing sensitive card data with non-sensitive tokens, reducing the scope of encryption requirements and minimizing breach risks.
Deterministic Encryption
Deterministic encryption enables consistent ciphertext generation from the same plaintext, providing reversible tokenization with searchable encrypted data, unlike traditional encryption which produces variable outputs.
PAN (Primary Account Number) Protection
Tokenization replaces the PAN with a non-sensitive token to minimize data exposure, while encryption transforms the PAN into an unreadable format requiring keys, both essential methods for robust PAN protection in payment processing.
Reversible Cryptography
Reversible cryptography enables secure data transformation where the original information can be restored, making it essential for encryption but less ideal for tokenization, which replaces data with non-reversible tokens to protect sensitive information without requiring decryption. Unlike encryption, tokenization reduces the risk of data breaches by storing sensitive data separately and ensuring tokens hold no exploitable value if intercepted.
Token Mapping
Token mapping bridges tokenization and encryption by converting sensitive data into non-sensitive tokens while preserving referential integrity without exposing original information.
Cryptographic Key Management
Cryptographic key management ensures secure generation, storage, and rotation of keys, critical for both tokenization and encryption to protect sensitive data and maintain compliance.
Surrogate Value Generation
Surrogate value generation creates unique placeholders during tokenization, enabling secure data substitution without encryption's computational overhead while preserving data usability and privacy compliance.
tokenization vs encryption Infographic
 moneydif.com
moneydif.com